Ransomware is not a new thing, but it is dominating the headlines. As we move into our second year of the Covid-19 pandemic, cyber attacks have escalated in frequency, sophistication, and creativity.
The recent attacks on the City of Baltimore and Colonial Pipeline in the US, Belgium’s Parliament, and Ireland’s Health Services demonstrate that ransomware has crossed a line. Once a financial threat limited to the corporate world, ransomware has officially become a global threat to national security.
So, why now do ransomware and other worldwide cyber threats have us over a barrel?
2020 Was A Perfect Storm Of Criminal Motive And Opportunity
Forced on businesses at the start of the global pandemic, we’ve seen the remote work experiment become a smashing success. So much so that many companies will continue a Work From Anywhere (WFX) model to reduce their brick-and-mortar footprint and have a happier workforce without stressful commutes.
We didn’t anticipate the enormous uptick in cyber attacks, ransomware, and staggering financial losses.

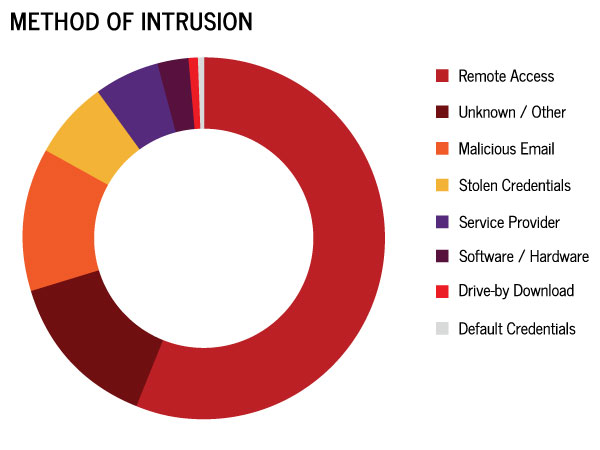
Unsecured RDP Is The Number One Problem
Covid-19 changed everything about how we work. In a rush to get business operations moving quickly, many businesses overlooked vital security controls.
Remote Desktop Protocol (RDP) allows people to access their office workstations from anywhere. It’s built into Microsoft Windows but also works with Apple, Android, and Linux devices.
Because it’s widely used for remote work, RDP has become a common conduit for bad actors to break into office networks easily.
Instead, switch to a Virtual Private Network (VPN) for employee remote access. It’s not perfect, but VPN adds another layer of security in remote access environments but must be combined with dual-factor authentication via mobile phone or email to be effective.
We Keep Making It Easier For Them
Stay-at-home isolation allows for the use of home workstations (no longer behind a centralized security stack) that mix business email and personal email accounts on poorly-secured home devices and networks.
Today’s WFX business model removes an essential layer of checks and balances due to the loss of contact with nearby team members. A typical example of funds transfer fraud (FTF) is when a spoofed email from the CFO directs the Controller to change the bank routing code for large wire transfers.
A Growing Data Breach Crisis
Analysis firm Canalys reports that attackers compromised more data records in 2020 than in the previous 15 years combined.
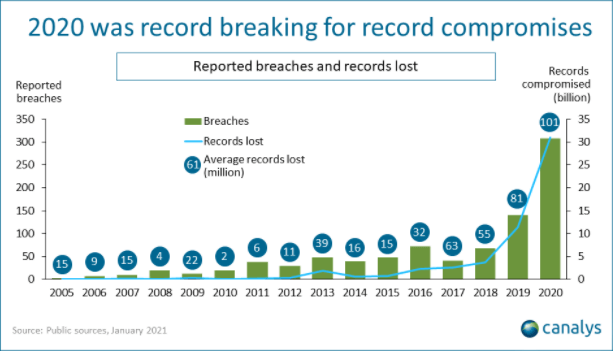
Ransomware Numbers in 2020
Cases of ransomware—a specific type of attack that encrypts files and shut down all business operations until they pay a ransom—have been on the rise, with the number of reported incidents up 60% compared to 2019.
2020 saw an exponential increase in the number and sophistication of available tools for cyber criminals.
Advances in computer performance and AI algorithms enable an onslaught of attacks. Something on the order of 3 billion email, SMS texting, and social media messages are sent every day by automated programs probing for cyber weakness.
What Are Stages Of A Ransomware Lifecycle?
Pre-2019 ransomware attacks were mostly smash-and-grab events. Individual attackers gain entry and quickly encrypt as much data as possible before the victim becomes aware of the intrusion. Then a lock screen pops up on user workstations demanding payment.
In 2020 we saw a steep escalation in better-organized ransomware attacks against high-value targets. These attacks are complex, and the timeline from beginning to end of a successful attack is measured in weeks, even months.

In cyber security, we use the term “dwell time” to describe the length of time attackers maintain systems control, unnoticed by defenders. Not every attack follows this precise format, but here are the typical stages of recent ransomware attacks:
Stages in a Ransomware Incident Lifecycle
| Stage | Approximate Time in Stage | Description |
| Pre-Breach Reconnaissance | Unlimited | Investigation and social engineering tactics uncover ways to trick a person at the target company into divulging login credentials or clicking a disguised link that contains malware. |
| Infection | Virtually instantaneous | The initial launch of malware on target systems. |
| Obfuscation | Less than 1 hour | Once penetrated, the attackers disguise the initial malware code to appear harmless and avoid detection. Traditional antivirus software is disabled. |
| Dwell time | Weeks – Months | This is an often-overlooked time that determines just how deep down the rabbit hole the attackers can advance before detection. Attackers take advantage of gathering information about the system they are attacking. Identification of data resources, folder structure, and whether backups exist internally. |
| Lateral Movement | Days – Weeks | Attackers broaden Command & Control (C2) and continue spreading the attack into connected systems. |
| Data Exfiltration | Hours – Days | Attackers download sensitive data for use in a double-extortion scheme, using stolen data to strengthen their position during ransom negotiation. |
| Encryption | Hours | This is where the hammer drops. After extracting valuable information, the attacker encrypts any backup volumes and then all the data files. |
| Ransom Negotiation | Various | Attackers negotiate payment parameters. How much. Which cryptocurrency. Disclosure of the amount and type of data that’s been stolen. Data shaming. Cyber taunting. Threatening phone calls. Whatever it takes to get paid. |
| Cleanup | As Needed | After the payment of ransom, many criminal groups offer customer service that will even help the victim restore their systems to pre-breach configuration. In theory. It’s important to know that attackers could stay connected for subsequent future attacks. |
Evolution of Ransomware
Cooperation between organized crime syndicates, advanced persistent threat (APT) criminal cartels, independent black hat actors—even nation-state operators—is at an all-time high. For example, in Russia, it’s not even considered a crime to extort businesses via ransomware unless used against Russian companies.
Attack Specialization By Stages
Honest businesses today hire “specialists” to fill positions within an organization. People bring diverse education and work experience—job roles they’re good at and may even enjoy doing 40+ hours a week.
This year we see similar hiring practices in these cyber syndicates to fill custom roles along the ransomware lifecycle. Ransom amounts have been ratcheting up to cover the increased workload for the biggest possible payout.
A customized ransomware attack needs highly technical individuals for malware code obfuscation and lateral movement during the dwell time. Social engineering specialists sift through social media profiles to uncover relevant personal information. Content teams craft phishing emails to lure the unwary to dangerous links or websites.
Project managers quarterback the entire attack process, and there’s even a customer service team to assist victims in regaining control of systems after paying the ransom.
Attack Specialization By Industry
Professional services firms are the number one targeted industry and account for one-third of known events. Lawyers, CPAs, and financial advisors top the list of “soft targets” because of their heavy dependence on data and its value on business operations. Lack of access to their data is crippling, and those services companies will pay up early and often.
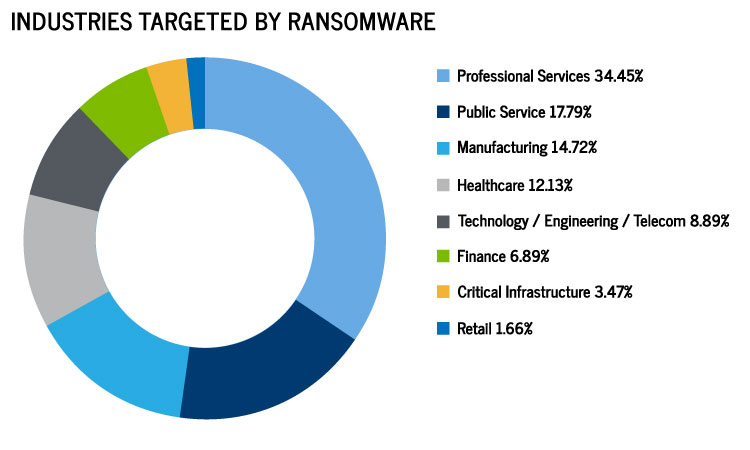
The manufacturing and healthcare sectors also contain high-value targets. Hospital systems and universities are gigantic institutions with a great deal of sensitive information on patients and students. The attackers threaten to publish this data unless the victim pays.
Larger ransomware groups employ industry specialists who understand how these mega institutions are structured and know just where to find the personally identifiable information (PII), efficiently sifting through thousands of terabytes of data.
Ransomware-as-a-Service
Not so long ago, a stereotypical “hacker” was a brilliant, high-tech loner who could bang out 200 words per minute on a keyboard and break into any company’s computer network with ease. Think, Neo in “The Matrix.”

By comparison, today’s criminal hacker doesn’t have to be particularly techno-savvy to make a living in cybercrime. Several Ransomware-as-a-Service (RaaS) operators advertise on the dark web and sell subscriptions to their targeted malware bundles for do-it-yourself-ers to take a crack at it.
Ransomware Insider Threats
Because cyber attacks take place every day, all over the world, more and more, an employee is found to be actively involved in helping attackers get information about an organization’s security posture.

With ransom amounts on the rise, criminal organizations have deep pockets to pay a cash finder’s fee to an employee for inserting a USB thumb drive containing malware into an office workstation. It’s just one more attack vector for companies to monitor.
Attackers Are Turning Up The Heat

Because of all the press surrounding ransomware of late, more and more businesses are actively shoring up their security defenses. Many have an up-to-date incident response plan (IRP) to quickly recover from an encryption ransomware attack using offsite backups and other recovery tools.
So, in response to this, attackers now use aggressive strongarm tactics to apply pressure and urgency to collect a ransom:
- Distributed Denial of Services (DDoS) attacks can crash cloud services that victims are using for recovery.
- Attackers take down a company’s public-facing websites, including ecommerce sites, that jeopardize both revenue and online reputation.
- Then comes data shaming, publishing personal data about the company’s C-Level execs. Addresses, salaries, family, social security numbers, etc.
- They secretly spy on a victim’s recovery efforts using already-compromised business email platforms.
- Most recently, they will call victims to taunt or threaten employees and their families.
Takeaways
The great news is that this year will mark the reopening of our society after being isolated for well over a year. Many businesses have maintained revenue and even grown during this Golden Age of the Remote Worker. Many businesses will continue a remote work model long after Covid-19 is in the rearview.
It’s important to recognize that ransomware criminal global infrastructure has blossomed in 2020 and won’t miss a beat even if everyone returns to their respective offices tomorrow. In conclusion, we encourage you to stay vigilant and have a plan in place. So, if you experience a breach or would like to develop a Business Cyber Incident Response Plan, we’re here to help.