
Business Email Compromise (BEC) is not the only flavor that today’s cyber-attacks come in, but it is the most common. And it’s become even more insidious in this Golden Age of the Remote Worker.
Quite simply, business email compromise (BEC) describes a cyber attack by professional criminals using a company’s email system to steal money or acquire proprietary business information for monetary gain. Surely by now, you’ve heard the term ”phishing” (and even know how to spell it).
Get our Ransomware Prevention & Response Guide

Here’s what you need to know and how to get started.
What’s at Stake?
Take a look at recent world-shaking events like SolarWinds, Microsoft, and FireEye. How this can happen to companies on the front lines of cyber security services is hard to get one’s head around. And yet, these corporations are still in business, functioning at a high level.
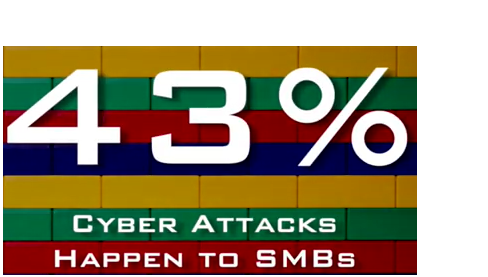
That said, 43% of successful cyber exploits happen to small- to medium-sized businesses (SMBs). Of those, 61% close their doors within a year. Please don’t assume that your business is too small to attract cyber criminals.
Examples of Business Email Compromise Techniques
Remember that these are professional criminals who continually tweak their process through trial and error, learning what works and what doesn’t. So, here are a few easy things to look for:

- Who sent you this email? Is this what previous emails from them look like? Do you know the sender? If you get an email from an acquaintance you haven’t communicated with in over ten years, it’s probably NOT from them. Their email has been compromised, and if you click on it, yours will be too.
- Email link spoofing. Hover your mouse over and examine any links in the email. Let’s say it’s from ABC Bank (membership@abcbank.com) and even has the bank’s logo and your correct mailing address. It seems legit, right? When you hover over the link or reply-to email address, does it still show “@abcbank.com,” or does it reveal the actual URL link as something like “abcbankmembership_@_jfh389fhj_4%*3#984hfgoanhfg0.ru”?
- CEO spoofing. You might see an urgent email “from” the CEO/President of your company asking you to do something innocuous like buying a gift card on the down low to give to a co-worker for a surprise promotion party.
- Fraudulent accounting requests. Wire fraud is especially dangerous and comes in the form of an email “from” your CFO (cc:’ing other high-level managers by name) authorizing you to change the “remit to” bank account for overseas wire transfers to your primary supplier.
Live in the Problem or Live in the Solution
First off, user education is often the best way to reduce the likelihood of a successful cyber-attack or lessen the impact if an attack does get through. Remember, for a criminal to hijack your email account, they only need you to drop your guard one time.
So, don’t ever give out personal information by email, text, or phone.
Because the IRS, Social Security Administration, Medicare, banks, credit card companies, charities, streaming video services—pretty much every legitimate business on the planet—would never ask you for personal info such as your DoB, SS#, account numbers, user ID, passwords, pin numbers, and the like.

Urgency + Poor Grammar = SCAM! 100% of the time.
Fraudsters use social engineering to manipulate people into giving up jackpot information. So don’t let them cash in on you.
Back in the day (wa-a-ay back), man’s instinctive response to a sense of urgency was very helpful to avoid being eaten by a saber-toothed tiger. But, today, an urgent response is a huge liability, in no way helpful to defend against 21st-century predators.

The next time it happens to you, remain calm. Respond, don’t react. Learn to TAKE A PAUSE. If you think to yourself, “maybe my credit card information has been stolen,” reach out to them by other means, not by clicking on the embedded link in the email or text that stirred you up.
A quick note on spelling and grammer grammar.
Email scams happen every day worldwide, millions of times in hundreds of languages. Consequently, scammers rely on automated engines to translate their dire payload into the local lingo.
So, if the text reads as a non-native English speaker wrote it, assume scam.

Ask yourself questions if something seems questionable.
If it feels wrong, it probably is. Pausing a few minutes or a few hours to calmly research and respond can’t hurt you if the message is genuine.
Be prepared as an organization.
Here are a few simple, inexpensive processes that a trusted IT security professional could put in place that can drastically reduce your attack surface or shrink the blast-damage area within your IT infrastructure.
- Multi-Factor Authentication (MFA). A secondary passcode is sent to you on a phone or other trusted device. So even if your password is compromised, the account is still secure.
- Long passwords (or passphrases) can keep nefarious AI from “brute-forcing” your short passwords. Length should be 12-15 characters minimum.
- Password rotation. If your LinkedIn password was hacked last year (along with millions of others), are you still using the same login credentials?
- Don’t reuse an identical password or passphrase for all of your personal accounts. Changing your behavior with a new password/passphrase model might seem a hassle, but the personal information you save might be your own.
So, ask for help.
If you’re not sure, ask your IT provider for their feedback. If you realize too late that you clicked on an email scam link, tell someone immediately. Many times a quick action could prevent a disastrous result.


