When using images found online, it’s not always 100% clear what can be used, how it can be used, and if accreditation is necessary.
What is clear, criminals are taking advantage of this lack of understanding.
Fake image copyright takedown requests are being sent to businesses via contact forms on websites.
The scam involves clever phishing emails warning that a particular image used on your company’s website is copyrighted material “owned by” the sender who threatens legal action if specific images are not immediately removed.
How exactly does this new scam work?
The user receives an email from an unknown sender who claims to be the registered owner of a particular image used without their permission on your company’s website contact form.
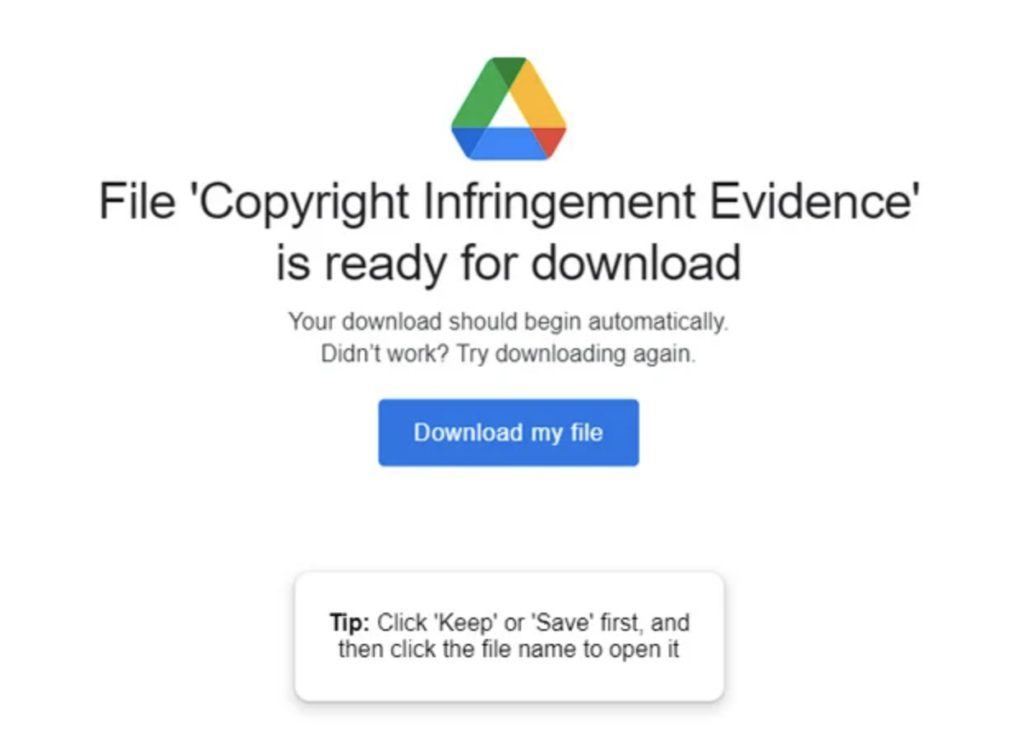
Fearing the worst, you click on the link contained in the email to investigate the supposed infraction.
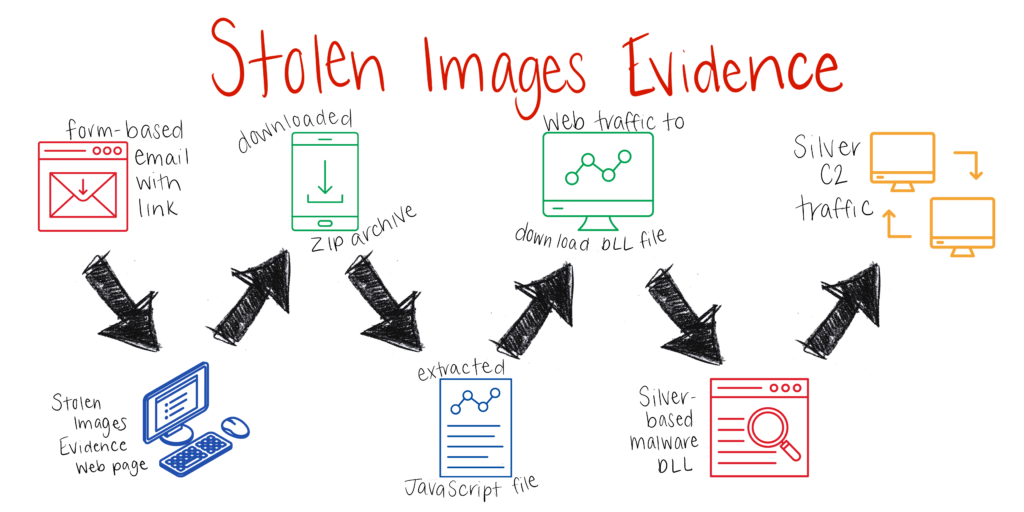
That link takes you to a fake “Stolen Images Evidence” web page and there’s a ZIP file you are asked to download and extract. The ZIP file contains malware that automatically installs on your workstation.
What makes this particular image copyright scam so dangerous for businesses?
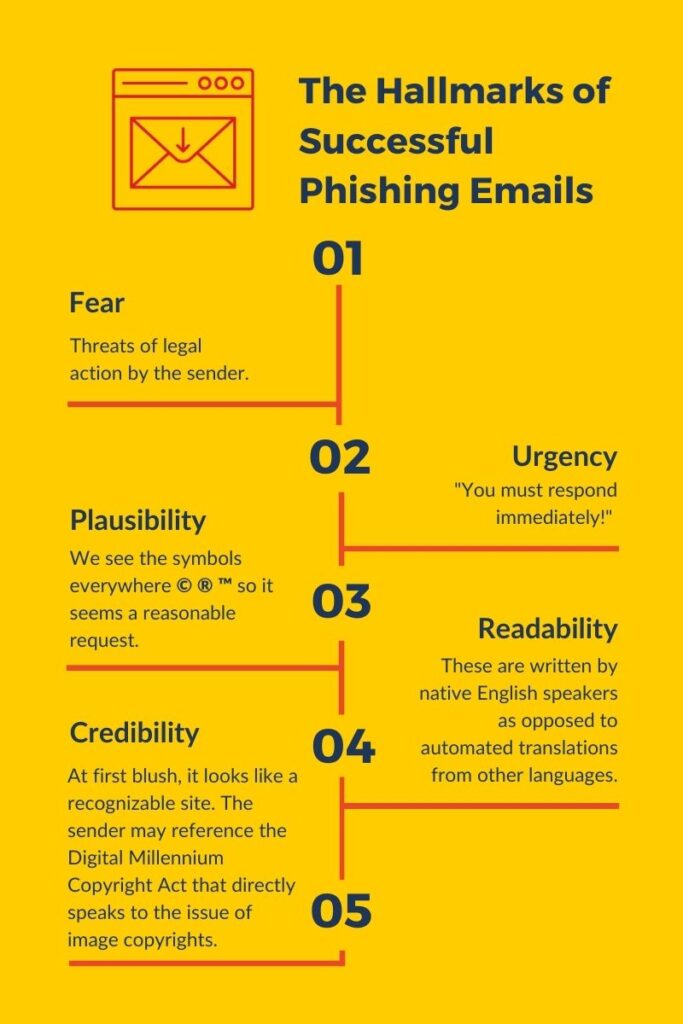
It contains all the hallmarks of successful phishing emails:
- Fear. Threats of legal action by the sender.
- Urgency. “You must respond immediately!”
- Plausibility. We see the symbols everywhere © ® ™ so it seems a reasonable request.
- Readability. These are written by native English speakers as opposed to automated translations from other languages.
- Credibility. At first blush, it looks like a recognizable site. The sender may reference the Digital Millennium Copyright Act that directly speaks to the issue of image copyrights.
It’s worth pointing out that digital marketing agencies that design websites take advantage of paid subscription services like Shutterstock, iStock, and many others that provide royalty-free images and other visual content for websites and blogs.
So it’s highly unlikely that any actual image copyright violations exist in today’s business landscape.
Who is most at risk to fall for this image copyright scam?
Persons in sales, marketing, and HR roles who monitor various internal “contact us” email addresses.

- info@yourcompany[.]com
- sales@yourcompany[.]com
- marketing@…
- hiring@…
- employment@…
- opportunities@…
- jobs@…
- admin@…
How can I protect my business now from this and other email scams?
The #1 reason this phishing tactic works: FEAR.
By creating an overwhelming sense of fear and urgency, our brains trigger a fight-or-flight-like response.

If you get something in your inbox from someone you don’t know telling you to “TAKE IMMEDIATE ACTION NOW!” by clicking a link or opening an attachment, STOP.
Takeaways
Business Email Compromise (BEC) is alive and well.
Bad actors are still using the pandemic work from home employee model to trick the unwary into opening emails that inject malware into their computers or mobile devices.
You can see a more detailed list of dos and don’ts of business email security hygiene here.
Remember, there is nothing that hits your inbox that can’t wait 10 minutes to consider and investigate.
Stay safe out there.


